OSINT Feeds
Our experimental "OSINT" Feeds cover most recent events reported by users on social websites like Twitter and Pastebin.
About
Find Out More About Us
Cyber Threat Intelligence is a process of collection, processing and analyzing the indicators of compromise for understanding attackers behavior and other TTP's.
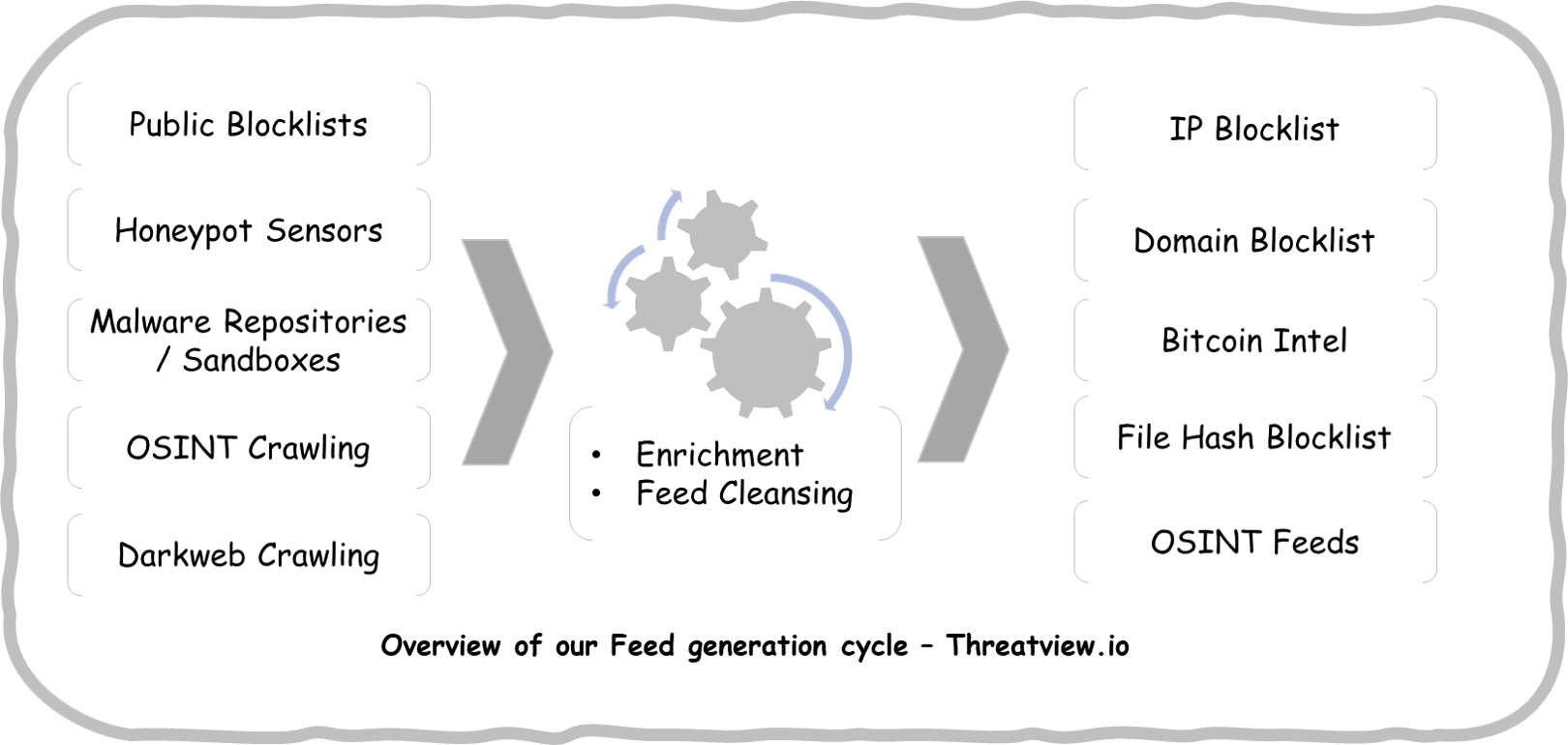
With the increase in cyber-attacks and new tactics, it is becoming increasingly difficult to identify malicious activities carried out by the attackers. Cyber Threat Watch is a Cyber Threat Intelligence Project (currently in beta) created for researching about cyber threat actors, campaigns and for supporting InfoSec community professionals to efficiently protect, identify and hunt malicious actors in IT environments. In order to simplify the process and provide actionable intelligence for rapid breach detection indicators of compromise in the form of IP, Domain, File Hash - MD5/SHA blocklists have been curated from Threat feeds using multiple sources including but not limited to the public blocklists, OSINT sources (Twitter and Pastebin), community threat feeds generated by individuals, organization(s) and honeypot(s).
Feed Sources
Hourly Feeds Generation
Million above IOC
Years of historic threat data
Feeds
Download our Threat Intelligence Feeds
The threat feeds are generated Daily@ 11 PM UTC, feeds with "High Confidence" in their names are likely to have less false positives.
Disclaimer: A significant amount of effort has been put to filter out false positives but the same is not assured, users are advised to ingest feed data after sufficient review and testing. Any data offered by our website is served as it is on best effort basis. We cannot be held liable for any false positive or damage caused by the use of the website or the datasets offered. All views expressed on this site are my own and do not represent the opinions of any entity whatsoever with which I have been, am now or will be affiliated.
OSINT Threat Feed
Malicious indicators of compromise gathered from OSINT Source - Twitter and Pastebin
C2 Hunt Feed
Infrastructure hosting Command & Control Servers found during Proactive Hunt by Threatview.io
MD5 Hash Blocklist
MD5 hashes of malicious files or associated with - malware, ransomware, hack tools, bots etc.
Use Cases
Check out some Use Cases
Threat feeds are in machine readable format and can be ingested readily in security appliances like firewalls, SIEM, Ad Blockers, PiHole etc. The Malicious Hash feeds can be ingested in Forensic tools readily by creating a hash set and then can be used for finding malicious files matching ingested hash values.
Threat feeds integration with PiHole
Pi-hole is a Linux network-level advertisement and Internet tracker blocking application which acts as a DNS sinkhole and optionally a DHCP server. PiHole can be integrated with our threat feeds using its inbuilt custom adlist feature. Login to your PiHole and add navigate to http://pihole-address/admin/groups-adlists.php. Create a new adlist with the URL of our domain and URL blocklist feed and add comment "Threatview.io - Custom Feed". PiHole will start to block all domains listed in our threat feeds for your protection.
Threat feeds integration with Security Appliances
Firewall, SIEM Solutions and other security appliances have inbuilt capability for addition of custom Blocklist/Blacklists/Threat feeds. We suggest using our Domain or IP threat feeds in your firewalls for additional detection and alerting. Security appliances have inbuilt features for automatic pull and update can also be used to stay upto date. We generate feeds every 24 hours except for our OSINT Feed, which is generated every 1 hour, you may configure your devices for scheduled automatic pull once in 24 hours or according to your preference. Perform Threat Hunting using our feeds on Azure Sentinel
Threat feeds integration with Forensics tools
Our threat intelligence feeds can assist Digital forensics and Incident response professionals in identifying malicious indicators of compromise on the digital device. Our MD5 Hash, SHA Hash and OSINT feed can be readily integrated in majority of commercial and opensource Forensics tools. Forensics professionals may utilize the functionality of "Ingest/Import Hash Sets" which will assist them in identifying files matching with the hashes from our threat feeds and will help in reducing overall turnaround time.F.A.Q
Frequently Asked Questions
-
What is the interval of Threat Feeds generation?
Threat Feeds are generated in 24hours at 11:00 PM UTC daily.
-
How can I use these threat feeds ?
Threat feeds are in machine readable format and can be ingested readily in security appliances like firewalls, SIEM, Ad Blockers, PiHole etc. The Malicious Hash feeds can be ingested in Forensic tools readily by creating a hash set and then can be used for finding malicious files matching ingested hash values. More information is available in Use Case section above.
-
I have noted some false positives from the feed, what should I do?
If you have noted any false positives, please send us an email and we will clear it out from the feeds. Collaboration and useful feedback are the key of supporting each other.
-
Are there any disclaimers or limitations ?
Any data offered by our website is served as it is on best effort. We cannot be held liable for any false positive or damage caused by the use of the website or the datasets offered. All views expressed on this site are my own and do not represent the opinions of any entity whatsoever with which I have been, am now or will be affiliated.
-
How can I contribute to the project?
We are open for collaboration, if you have any indicators of compromise or working on a campaign and need hands. Please feel free to reach out on our email or Twitter.
Contact
Contact Us
If you have any suggestions, indicators of compromise, report false positives or want to get in touch
Email Us
feeds@threatview[.]io